An operating system (OS) is a collection of software that manages computer hardware resources and provides common services for computer programs. The operating system is a vital component of the system software in a computer system.Operating System
An Operating System (OS) is an interface between a computer user and computer hardware. An operating system is a software which performs all the basic tasks like file management, memory management, process management, handling input and output, and controlling peripheral devices such as disk drives and printers.
Some popular Operating Systems include Linux, Windows, OS X, VMS, OS/400, AIX, z/OS, etc.
Definition
An operating system is a program that acts as an interface between the user and the computer hardware and controls the execution of all kinds of programs.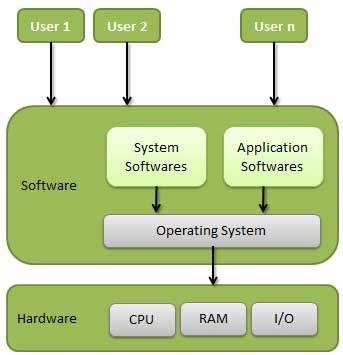
TYPES OF OPERATING SYSTEM
Batch operating system
The users of a batch operating system do not interact with the computer directly. Each user prepares his job on an off-line device like punch cards and submits it to the computer operator. To speed up processing, jobs with similar needs are batched together and run as a group. The programmers leave their programs with the operator and the operator then sorts the programs with similar requirements into batches.The problems with Batch Systems are as follows −
- Lack of interaction between the user and the job.
- CPU is often idle, because the speed of the mechanical I/O devices is slower than the CPU.
- Difficult to provide the desired priority.
Time-sharing operating systems
Time-sharing is a technique which enables many people, located at various terminals, to use a particular computer system at the same time. Time-sharing or multitasking is a logical extension of multi programming. Processor's time which is shared among multiple users simultaneously is termed as time-sharing.The main difference between Multi programmed Batch Systems and Time-Sharing Systems is that in case of Multi programmed batch systems, the objective is to maximize processor use, whereas in Time-Sharing Systems, the objective is to minimize response time.
Multiple jobs are executed by the CPU by switching between them, but the switches occur so frequently. Thus, the user can receive an immediate response. For example, in a transaction processing, the processor executes each user program in a short burst or quantum of computation. That is, if n users are present, then each user can get a time quantum. When the user submits the command, the response time is in few seconds at most.
The operating system uses CPU scheduling and multi-programming to provide each user with a small portion of a time. Computer systems that were designed primarily as batch systems have been modified to time-sharing systems.
Advantages of Time sharing operating systems are as follows −
- Provides the advantage of quick response.
- Avoids duplication of software.
- Reduces CPU idle time.
- Problem of reliability.
- Question of security and integrity of user programs and data.
- Problem of data communication.
Distributed operating System
Distributed systems use multiple central processors to serve multiple real-time applications and multiple users. Data processing jobs are distributed among the processors accordingly.The processors communicate with one another through various communication lines (such as high-speed buses or telephone lines). These are referred as loosely coupled systems or distributed systems. Processors in a distributed system may vary in size and function. These processors are referred as sites, nodes, computers, and so on.
The advantages of distributed systems are as follows −
- With resource sharing facility, a user at one site may be able to use the resources available at another.
- Speedup the exchange of data with one another via electronic mail.
- If one site fails in a distributed system, the remaining sites can potentially continue operating.
- Better service to the customers.
- Reduction of the load on the host computer.
- Reduction of delays in data processing.
Network operating System
A Network Operating System runs on a server and provides the server the capability to manage data, users, groups, security, applications, and other networking functions. The primary purpose of the network operating system is to allow shared file and printer access among multiple computers in a network, typically a local area network (LAN), a private network or to other networks.Examples of network operating systems include Microsoft Windows Server 2003, Microsoft Windows Server 2008, UNIX, Linux, Mac OS X, Novell NetWare, and BSD.
The advantages of network operating systems are as follows −
- Centralized servers are highly stable.
- Security is server managed.
- Upgrades to new technologies and hardware can be easily integrated into the system.
- Remote access to servers is possible from different locations and types of systems.
- High cost of buying and running a server.
- Dependency on a central location for most operations.
- Regular maintenance and updates are required.
Real Time operating System
A real-time system is defined as a data processing system in which the time interval required to process and respond to inputs is so small that it controls the environment. The time taken by the system to respond to an input and display of required updated information is termed as the response time. So in this method, the response time is very less as compared to online processing.Real-time systems are used when there are rigid time requirements on the operation of a processor or the flow of data and real-time systems can be used as a control device in a dedicated application. A real-time operating system must have well-defined, fixed time constraints, otherwise the system will fail. For example, Scientific experiments, medical imaging systems, industrial control systems, weapon systems, robots, air traffic control systems, etc.
There are two types of real-time operating systems.
Hard real-time systems
Hard real-time systems guarantee that critical tasks complete on time. In hard real-time systems, secondary storage is limited or missing and the data is stored in ROM. In these systems, virtual memory is almost never found.Soft real-time systems
Soft real-time systems are less restrictive. A critical real-time task gets priority over other tasks and retains the priority until it completes. Soft real-time systems have limited utility than hard real-time systems. For example, multimedia, virtual reality, Advanced Scientific Projects like undersea exploration and planetary rovers, etc.Classification of Operating systems
Utility software is system software designed to help analyze, configure, optimize or maintain a computer.[1] It is a type of system software, used to support the computer infrastructure;[2] by contrast with application software, which is aimed at directly performing tasks that benefit ordinary users.
Types of utilities
- Anti-virus utilities scan for computer viruses.
- Archivers output a stream or a single file when provided with a directory or a set of files. Archive suites may include compression and encryption capabilities. Some archive utilities have a separate un-archive utility for the reverse operation.
- Backup software makes copies of all information stored on a disk and restore either the entire disk (e.g. in an event of disk failure) or selected files (e.g. in an event of accidental deletion).
- Clipboard managers expand the clipboard functionality of an operating system .
- Cryptographic utilities encrypt and decrypt streams and files.
- Data compression utilities output a shorter stream or a smaller file when provided with a stream or file.
- Data synchronization
utilities establish consistency among data from a source to a target
data storage and vice versa. There are several branches of this type of
utility:
- File synchronization utilities maintain consistency between two sources. They may be used to create redundancy or backup copies but are also used to help users carry their digital music, photos and video in their mobile devices.
- Revision control utilities can recreate a coherent structure where multiple users simultaneously modify the same file.
- Disk checkers scan an operating hard drive and check for logical (filesystem) or physical errors.
- Disk cleaners find files that are unnecessary to computer operation, or take up considerable amounts of space. Disk cleaner helps the user to decide what to delete when their hard disk is full.
- Disk compression utilities transparently compress/uncompress the contents of a disk, increasing the capacity of the disk.
- Disk defragmenters detect computer files whose contents are scattered across several locations on the hard disk, and move the fragments to one location to increase efficiency.
- Disk partition editors divide an individual drive into multiple logical drives, each with its own file system which can be mounted by the operating system and treated as an individual drive.
- Disk space analyzers provide a visualization of disk space usage by getting the size for each folder (including sub folders) & files in folder or drive. showing the distribution of the used space.
- File manager provide a convenient method of performing routine data management, email recovery and management tasks, such as deleting, renaming, cataloging, uncataloging, moving, copying, merging, generating and modifying folders and data sets.
- Hex editors directly modify the text or data of a file. These files could be data or an actual program.
- Memory testers check for memory failures.
- Network utilities analyze the computer's network connectivity, configure network settings, check data transfer or log events.
- Package managers are used to configure, install or keep up to date other software on a computer.
- Registry cleaners clean and optimize the Windows Registry by removing old registry keys that are no longer in use.
- Screensavers were desired to prevent phosphor burn-in on CRT and plasma computer monitors by blanking the screen or filling it with moving images or patterns when the computer is not in use. Contemporary screensavers are used primarily for entertainment or security.
- System monitors monitor resources and performance in a computer system.
- System profilers provide detailed information about the software installed and hardware attached to the computer.
Following are some of important functions of an operating System.
- Memory Management
- Processor Management
- Device Management
- File Management
- Security
- Control over system performance
- Job accounting
- Error detecting aids
- Coordination between other software and users
Memory Management
Memory management refers to management of Primary Memory or Main Memory. Main memory is a large array of words or bytes where each word or byte has its own address.Main memory provides a fast storage that can be accessed directly by the CPU. For a program to be executed, it must in the main memory. An Operating System does the following activities for memory management −
- Keeps tracks of primary memory, i.e., what part of it are in use by whom, what part are not in use.
- In multiprogramming, the OS decides which process will get memory when and how much.
- Allocates the memory when a process requests it to do so.
- De-allocates the memory when a process no longer needs it or has been terminated.
Processor Management
In multiprogramming environment, the OS decides which process gets the processor when and for how much time. This function is called process scheduling. An Operating System does the following activities for processor management −- Keeps tracks of processor and status of process. The program responsible for this task is known as traffic controller.
- Allocates the processor (CPU) to a process.
- De-allocates processor when a process is no longer required.
Device Management
An Operating System manages device communication via their respective drivers. It does the following activities for device management −- Keeps tracks of all devices. Program responsible for this task is known as the I/O controller.
- Decides which process gets the device when and for how much time.
- Allocates the device in the efficient way.
- De-allocates devices.
File Management
A file system is normally organized into directories for easy navigation and usage. These directories may contain files and other directions.An Operating System does the following activities for file management −
- Keeps track of information, location, uses, status etc. The collective facilities are often known as file system.
- Decides who gets the resources.
- Allocates the resources.
- De-allocates the resources.
Other Important Activities
Following are some of the important activities that an Operating System performs −- Security − By means of password and similar other techniques, it prevents unauthorized access to programs and data.
- Control over system performance − Recording delays between request for a service and response from the system.
- Job accounting − Keeping track of time and resources used by various jobs and users.
- Error detecting aids − Production of dumps, traces, error messages, and other debugging and error detecting aids.
- Coordination between other softwares and users − Coordination and assignment of compilers, interpreters, assemblers and other software to the various users of the computer systems.
Compiler: It is a program which translates a high level language program into a
machine language program. A compiler is more intelligent than an assembler. It
checks all kinds of limits, ranges, errors etc. But its program run time is
more and occupies a larger part of the memory. It has slow speed. Because a
compiler goes through the entire program and then translates the entire program
into machine codes. If a compiler runs on a computer and produces the machine
codes for the same computer then it is known as a self compiler or resident
compiler. On the other hand, if a compiler runs on a computer and produces the
machine codes for other computer then it is known as a cross compiler.
Interpreter: An interpreter is a program which translates statements of a program into machine code. It translates only one statement of the program at a time. It reads only one statement of program, translates it and executes it. Then it reads the next statement of the program again translates it and executes it. In this way it proceeds further till all the statements are translated and executed. On the other hand, a compiler goes through the entire program and then translates the entire program into machine codes. A compiler is 5 to 25 times faster than an interpreter.
By the compiler, the machine codes are saved permanently for future reference. On the other hand, the machine codes produced by interpreter are not saved. An interpreter is a small program as compared to compiler. It occupies less memory space, so it can be used in a smaller system which has limited memory space.
Linker: In high level languages, some built in header files or libraries are stored. These libraries are predefined and these contain basic functions which are essential for executing the program. These functions are linked to the libraries by a program called Linker. If linker does not find a library of a function then it informs to compiler and then compiler generates an error. The compiler automatically invokes the linker as the last step in compiling a program.
Not built in libraries, it also links the user defined functions to the user defined libraries. Usually a longer program is divided into smaller subprograms called modules. And these modules must be combined to execute the program. The process of combining the modules is done by the linker.
Loader: Loader is a program that loads machine codes of a program into the
system memory. In Computing, a loader is the part of an Operating System that is
responsible for loading programs. It is one of the essential stages in the
process of starting a program. Because it places programs into memory and
prepares them for execution. Loading a program involves reading the contents of executable file into memory. Once loading is complete, the
operating system starts the program by passing control to the loaded program
code. All operating systems that support program loading have loaders. In many
operating systems the loader is permanently resident in memory.
Assembler: A computer will not understand any program written in a language, other than its machine language. The programs written in other languages must be translated into the machine language. Such translation is performed with the help of software. A program which translates an assembly language program into a machine language program is called an assembler. If an assembler which runs on a computer and produces the machine codes for the same computer then it is called self assembler or resident assembler. If an assembler that runs on a computer and produces the machine codes for other computer then it is called Cross Assembler.
DOS OPERATION
The literal definition is that MS-DOS stands for "Microsoft Disk
Operating System". The answer most readers are looking for is that DOS
is a command-line method of executing basically the same functions
available in Windows. The main difference is the lack of wizards, the
need to be precise, and the fact that DOS came first. However, DOS has
much more power than your standard Windows, and if you know the right
commands, you can get information much more quickly. With this in mind,
let us begin...
THE BASICS OF MS-DOS
Navigating folders and Simple Commands
Depending on whether you are using the Prompt or "true DOS", you should see a prompt similar to this:
C:\>
or this:
C:\Documents and Settings\Yourname>
Regardless, you are ready to get started.
Seeing what is in your current directory
Obviously, you have to be able to see what you're doing or else you are "shooting in the dark" with no idea what to do. Luckily, there is a command to show what is in your current directory. Type DIR and press [Enter] to activate this fuction. It should look like this:
C:\>DIR
The results I got in C:\ were:
Volume in drive C has no label.
Volume Serial Number is 8C87-FFA1
Directory of C:\
04/18/2006 12:06 AM 0 AUTOEXEC.BAT
04/21/2006 04:42 PM <DIR> Batch
04/18/2006 12:06 AM 0 CONFIG.SYS
04/18/2006 12:21 AM 32 csb.log
04/21/2006 07:45 PM 0 dir.txt
04/18/2006 12:12 AM <DIR> Documents and Settings
04/18/2006 12:45 AM <DIR> NVIDIA
04/21/2006 04:27 PM <DIR> Program Files
04/20/2006 08:01 PM <DIR> WINDOWS
4 File(s) 32 bytes
5 Dir(s) 196,047,323,136 bytes free
The items with <DIR> are directories, or folders. Anything else is a file. The column on the left is the date the files were last changed, the next column shows the time the files were modified. The number to the left of the file name is the size of the file in bytes.
If there are too many directories to list on one screen, type one of the following commands:
DIR /w
OR
DIR /p
The /w switch makes the DIR appear in a wider format, while /p displays the DIR one screenful at a time.
Changing directories
OK, you want to leave the directory you're in. No matter how exciting it gets, C:\ isn't going to be exciting enough as there is not all the information you need in the root. To change directories, type CHDIR [directory name] or CD [directory name], replacing [directoryname] with the name of the directory you wish to go to. So, on my pc, if I want to change to C:\NVIDIA, I type
C:\>CD NVIDIA
The prompt changes to
C:\NVIDIA>
Opening files
In the Command Prompt, these files will run outside of cmd.exe. In true DOS, this is obviously not the case, but only DOS-friendly files may be run. To open an EXE file, simply type the name of the EXE file, and it will run. So, If I'm in C:\Program Files\Chami\HTML-Kit\ and I want to run HTML-Kit from Command prompt, I would type
C:\Program Files\Chami\HTML-Kit>HTML-Kit.EXE
and the program would run. To access a text file, you would use the TYPE command:
C:\>TYPE dir.txt
and the information would display on my command screen. Note, however, that some text files may be too long for the screen. For files like this, type the following command:
C:\>TYPE dir.txt | more
Replacing dir.txt with the name of the file you want to display. The | key is found above the [Enter] key ([Shift] and \). When the file reaches the size of the page, it will pause, asking you to press [Enter]. Pressing [Enter] will move the page down one line. If you change your mind partway through reading the long file, Press [Ctrl] and C. You will go back to the prompt.
The TYPE command works with virtually any kind of file, but note that you will not be able to read all of them. Compiled EXE files will show strange characters, as will .dat and other files. Do not worry, no harm is done.
Clearing the screen
If you don't like clutter, press CLS at any time. This command clears the screen of everything but the latest prompt.
Creating files
So far, if you are following this tutorial in a linear fashion, you have not changed anything; you have only taken a look at how the files are stored and where. Here, you will learn two ways of adding to your system in a way that cannot harm your system at all: Creating files.
This is a part of MS-DOS that is more powerful than Windows. In Windows, you can only create the extensions listed on the "New" menu. In MS-DOS, you can create any file extension you want, including extensions not recognized by Windows. They can still be read, however, from Windows if you open it with a program like Notepad.
To create a file using the Copy Con method, type at the prompt:
COPY CON Newfile.txt
Replace Newfile.txt with any file name and extension you choose and press [Enter]. At first, nothing will seem to happen. You will need to press [Control] and Z. The symbol ^Z will appear. Press [Enter] to confirm. What you see should resemble this when you are done:
C:\>COPY CON newfile.txt
^Z
1 file(s) copied.
C:\>
Another method is the Edit method. Simply type:
EDIT newfile.txt
You will be taken to a blue window, MS-DOS's first attempt at a GUI. Type whatever you want, then go to File and click Save. Then go back into File and click Exit. The file is created.
A note about the EDIT method: If the file already exists, you will see that file's contents instead of a blank blue screen. It is not recommended that you change what's there unless you know what you are doing.
Moving files
Let's say you have a file in C:\ but it needs to be in C:\Pictures. You could copy it, and then go back and delete the original. But there is an easier solution.
NOTE: I cannot verify this, but I believe that some really really old versions of DOS do not support a MOVE command. If you are one of these accursed (
 )
people, I have written a batch file called XMOVE. It's as versatile as
MOVE and has the same syntax, except no switches are available for
XMOVE. Download XMOVE here. Stick the .BAT file in C:\WINDOWS\System32 as a quick install.
)
people, I have written a batch file called XMOVE. It's as versatile as
MOVE and has the same syntax, except no switches are available for
XMOVE. Download XMOVE here. Stick the .BAT file in C:\WINDOWS\System32 as a quick install.The MOVE command is exactly like Copy, except that the original, the source, is deleted. The syntax is:
MOVE [source] [destination]
The only switches are the /Y and /-Y, which serve the same function as the /Y and /-Y in the COPY command. As with COPY, you can move multiple files elsewhere.
IP information
As you may know, your IP address is your unique computer signature on the net. Even if your PC does not have access to the Internet, you still have an IP address for "just in case". Sometimes, it is necessary to retrieve or modify this information. To see all the information you will need, use the command
ipconfig /all
This will display, among other things, your IP address, Subnet Mask, Default Gateway, etc.. You should also see info about any Ethernet Adpapters or Wireless Adapters you have. You may or may not have more than one adapter; most PC's just have the one.
So, if you need to renew your IP address in order to troubleshoot or some such thing, type
ipconfig /release
If you have more than one adapter, specify the number of the adapter like so:
ipconfig /release 0
replacing 0 with the number of your adapter. This command gets rid of your IP address. Now, type
ipconfig /renew
if you specified a number when you released, then you should specify that same number again.
Attributes
For whatever reason, you may want to make it so that nobody can modify a file. Or, maybe hide it from view. This is where the ATTRIB command comes in handy.
The use of this command varies from Operating System to Operating System, but they are similar:
In Windows 9x and Windows ME:
+ - adds attribute.
- - Removes attribute
R - Read-only (cannot be modified while attribute is set)
ATTRIB +R nochange.txt (adds attribute)
ATTRIB -R change.txt (removes attribute)
A - Archive
S - System file
H - Hidden file
/S - Sets attribute to all files in all folders in specified path.
ATTRIB +H file.txt /S (sets all files in current directory and below as hidden)
In Windows 2000 or XP:
Same as Win95, 98 and ME with one addition:
/D - makes all folders this attribute as well.
In Win2000 or WinXP Recovery Console:
Same as above except:
1. The Archive attribute is unavailable
2. The /S and /D switches are unavailable
3. The Compressed attribute is available (ATTRIB +C file.txt)
As you may know, your IP address is your unique computer signature on the net. Even if your PC does not have access to the Internet, you still have an IP address for "just in case". Sometimes, it is necessary to retrieve or modify this information. To see all the information you will need, use the command
ipconfig /all
This will display, among other things, your IP address, Subnet Mask, Default Gateway, etc.. You should also see info about any Ethernet Adpapters or Wireless Adapters you have. You may or may not have more than one adapter; most PC's just have the one.
So, if you need to renew your IP address in order to troubleshoot or some such thing, type
ipconfig /release
If you have more than one adapter, specify the number of the adapter like so:
ipconfig /release 0
replacing 0 with the number of your adapter. This command gets rid of your IP address. Now, type
ipconfig /renew
if you specified a number when you released, then you should specify that same number again.
Attributes
For whatever reason, you may want to make it so that nobody can modify a file. Or, maybe hide it from view. This is where the ATTRIB command comes in handy.
The use of this command varies from Operating System to Operating System, but they are similar:
In Windows 9x and Windows ME:
+ - adds attribute.
- - Removes attribute
R - Read-only (cannot be modified while attribute is set)
ATTRIB +R nochange.txt (adds attribute)
ATTRIB -R change.txt (removes attribute)
A - Archive
S - System file
H - Hidden file
/S - Sets attribute to all files in all folders in specified path.
ATTRIB +H file.txt /S (sets all files in current directory and below as hidden)
In Windows 2000 or XP:
Same as Win95, 98 and ME with one addition:
/D - makes all folders this attribute as well.
In Win2000 or WinXP Recovery Console:
Same as above except:
1. The Archive attribute is unavailable
2. The /S and /D switches are unavailable
3. The Compressed attribute is available (ATTRIB +C file.txt)
Operating System Virtualization (OS Virtualization)
Operating
system virtualization (OS virtualization) is a server virtualization
technology that involves tailoring a standard operating system so that
it can run different applications handled by multiple users on a single
computer at a time. The operating systems do not interfere with each
other even though they are on the same computer.
In OS virtualization, the operating system is altered so that it operates like several different, individual systems. The virtualized environment accepts commands from different users running different applications on the same machine. The users and their requests are handled separately by the virtualized operating system.
Also known as operating system-level virtualization.
In OS virtualization, the operating system is altered so that it operates like several different, individual systems. The virtualized environment accepts commands from different users running different applications on the same machine. The users and their requests are handled separately by the virtualized operating system.
Also known as operating system-level virtualization.
No comments:
Post a Comment